- Find the “model text” that you want to use as the AutoText entry and copy it into your Windows clipboard (CTRL+C) (this could be a frequent paragraph or short phrase that you type often in numerous responses. Draft a new email and paste it into the body of the new email. Format it and clean it up to the format you want it in (bullets, numbered, paragraphs, etc). We suggest removing any client names to make it generic.
- Select the text and then select Insert > Quick Parts > AutoText > Save Selection to AutoText to AutoText Gallery
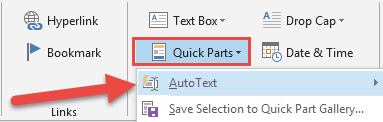
- Give it a name (nickname) with at least 4 characters.
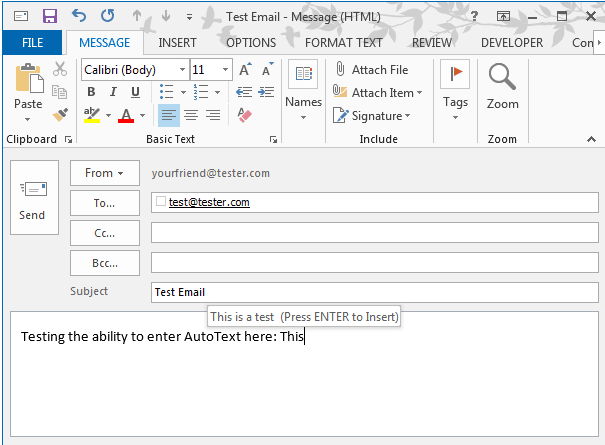
- To use the AutoText entry, simply place your cursor in the body of the email (in the desired location), and then type the first 4 characters of the AutoText name. You will see a pop-up preview of your entry. If you want to insert it, simply hit your Enter key. Another way to insert it is to select Insert > Quick Parts > AutoText > and then select the AutoText entry from the preview gallery.
New Resources In Your Inbox
Get our latest cybersecurity resources, content, tips and trends.

Other resources that might be of interest to you.
Phishing Awareness
Phishing Phishing attacks use email or malicious websites to infect your machine with malware and viruses to collect personal and financial information. Cybercriminals attempt to lure users to click on a link or open an attachment that infects their co
Alan Villasenor
>>Read More
Podcast: In the Ransomware Recovery Trenches
Episode Summary The impact of ransomware on organizations is well-known. Companies can be coerced into making ransom payments. The business itself could be forced to close. Sensitive customer data can be leaked onto the Dark Web. An impacted organizati
Conor Quinlan
>>Read More
Podcast: Basics of Cybersecurity and What You’re Securing
In our latest podcast, Basics of Cybersecurity and What You’re Securing, we interviewed Pat Gorman, a seasoned cybersecurity professional. With over 18 years in IT, he shares valuable insights for aspiring professionals. Pat excels in team man
Vivian Lee
>>Read More
