Defend Your Business: Webinar Summary
Airiam and Eviden wrapped up the second of our Threat Actors webinar series! Art Ocain and Dwayne Robinson were great hosts walking us through a ton of information.
Scenario
On a normal Tuesday morning, you start up your computer to work, but your application suddenly freezes. You then see all files on your computer end in “.fried”
You then see a RANSOMNOTE.txt file in every folder.
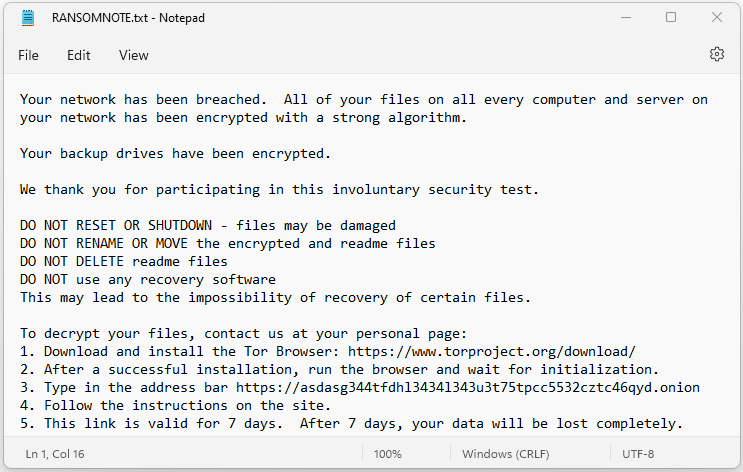
What should you do to defend your business?
The first things you should NOT do are:
- Turn off all your computers and servers
- Call 911
- Get your wallet out and pay the ransom
- Put a PSA about the breach in your local newspaper, Twitter (or X), or other mass, public notifications.
The Right Way
As a preface, everyone should know that the right way is not cheap or easy. If it was, everyone would be able to do it and experts wouldn’t be needed.
When you realize your business has been breached, you should:
|
|
Make sure to discuss with your lawyer before any communication with PR or law enforcement. While this might sound counterintuitive, the goals of law enforcement and the goals of your business do not coincide. Law enforcement’s goal is to find and prosecute the attackers, not get your data back or get you up and running again.
SANS Incident Response Process
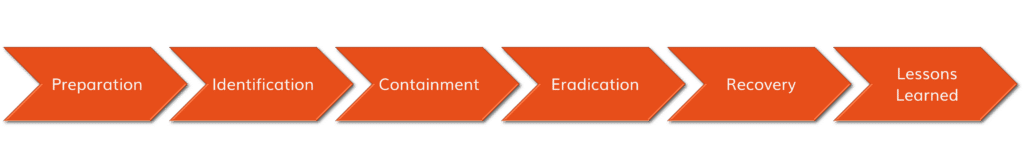
Preparation
Determine how you will respond to an incident. Make a plan and prepare.
- Collect an inventory of assets (your computers, servers, cloud services, usernames/passwords)
- Create a prioritized list of IT systems, services, and data locations
- Create an incident response plan
- Create backup/restore strategy
- Improve defenses (MFA, endpoint detection & response, next-gen firewall, etc.)
- Determine who you are calling for help
Identification
How do you know if you’ve been breached? Look for these signs:
- Ransomware: Encrypted files, ransom notes
- Business Email Compromise (BEC): People let you know that they receive emails from you (impersonation), fraud is performed as you, you find that information has been breached or stolen from your email account
- Phishing: Unprompted password reset requests, identity theft, locked accounts, unfamiliar transactions [note that phishing is usually a component of Business Email Compromise (BEC)]
- Breach: Anomalies on your systems (new accounts, etc.), systems are being used at strange times, your data is found on the Internet
Containment
Stop the threat from creating further damage! IMMEDIATELY AFTER AN ATTACK, start with isolating affected systems and creating an air gap in the breach/ransomware.
- Disconnect infected computers from the network (Ethernet & Wifi).
- Unplug the Internet from your router to kick the attacker out.
- DO NOT continue to use them and DO NOT connect to a hotspot. The attacker can access your computer.
- If there is spread between computers (a worm or other lateral movement from a hacker), unplug each computer individually, you can unplug the core switches in your network closet.
- Avoid shutting down as malware often runs in memory now.
- Protect your backups. Immediately unplug your backup storage (USB hard drives or network-attacked storage).
If you are not sure which computers/servers were impacted, assume that ALL systems are infected or compromised.
Eradication
Begin to eliminate the threat and the root cause of the attack.
- Disable compromised accounts
- Disable the accounts that the attackers used.
- Verify that there are no forwarders or rules sending a copy of your email to an attacker. Check password recovery/MFA methods for compromise.
- Change ALL passwords [in all forms of attack: BEC/phishing/breach/ransomware
- From a clean, uncompromised computer, change ALL your passwords: email, financial sites, network passwords, wireless, etc. Flush Kerberos ticket – twice.
- Make sure that you use a different password for EVERY site.
- Deploy MFA [in all forms of attack: BEC/phishing/breach/ransomware]
- Deploy multifactor authentication (MFA) on your email, your VPN, and other applications.
- Put in firewall rules before plugging the Internet back in [in breach/ransomware]
- Block remote desktop (RDP) [no exceptions – this is a gaping hole]
- Block compromised applications and command-and-control servers.
- Deploy geo-blocking (block non-US locations) if possible.
- Use Next-Gen Firewall features (automatic threat blocking). Throw non-NGFWs in the dumpster.
- Deploy an Endpoint Detection & Response (EDR) tool [in breach/ransomware]
- Have a cybersecurity professional configure your EDR to automatically quarantine your threats and isolate machines under attack.
- Install EDR on every computer and server.
- Patch Vulnerabilities
- Install all Windows updates and 3rd party security patches.
- Upgrade firewall software.
- Upgrade wireless software.
For all of these points, use a SECURITY PROFESSIONAL.
Recovery
Once the threat has been eradicated, you can then work on recovering your files and restoring your business.
- Rebuild, restore, or decrypt
- Restore any servers/computers from backup from before the attack.
- Reinstall any servers/computers from scratch that have no backup.
- If you paid a ransom, decrypt the computers to obtain your data. Remember that the machines you decrypt are still compromised.
- Assess compromised accounts which you disabled
- Determine whether you want to create new user accounts to replace any compromised accounts, or whether you will risk using your old accounts.
Lessons Learned
Finally, the last steps in all of this are to review and improve. Improve your incident response plan and your cybersecurity strategy and solutions.
Register for More Webinars
Register for our next webinars! Airiam is hosting our next series of webinars in collaboration with our partners! Each partner will help us walk through 4 key moments of a threat actor attack. Next up is “How to Rebuild Your Company After an Attack” with MOXFIVE.
| DATE | TOPIC | PARTNER | REGISTER |
| July 19, 11AM EST | Live Attack Simulation |  |
Watch Here |
| August 29, 12PM EST | How to Defend Your Company During an Attack |  |
Watch Here |
| September 19, 12PM EST | How to Rebuild Your Company After an Attack |  |
Register Here |
| October 11, 11AM EST | How to Prepare Your Company for Future Attacks | Register Here |


