- Find the “model text” that you want to use as the AutoText entry and copy it into your Windows clipboard (CTRL+C) (this could be a frequent paragraph or short phrase that you type often in numerous responses. Draft a new email and paste it into the body of the new email. Format it and clean it up to the format you want it in (bullets, numbered, paragraphs, etc). We suggest removing any client names to make it generic.
- Select the text and then select Insert > Quick Parts > AutoText > Save Selection to AutoText to AutoText Gallery
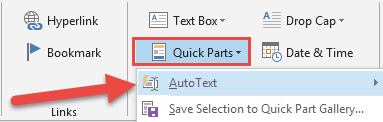
- Give it a name (nickname) with at least 4 characters.
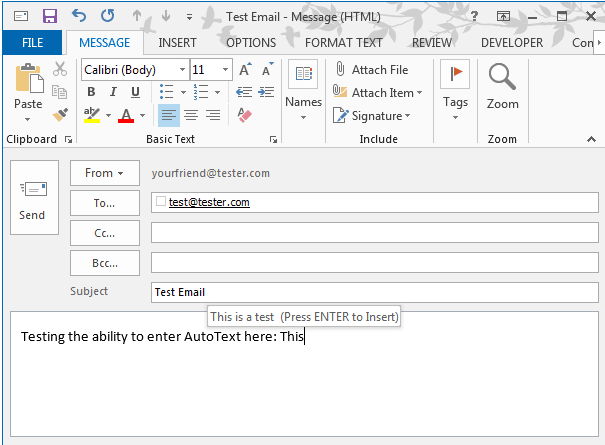
- To use the AutoText entry, simply place your cursor in the body of the email (in the desired location), and then type the first 4 characters of the AutoText name. You will see a pop-up preview of your entry. If you want to insert it, simply hit your Enter key. Another way to insert it is to select Insert > Quick Parts > AutoText > and then select the AutoText entry from the preview gallery.
New Resources In Your Inbox
Get our latest cybersecurity resources, content, tips and trends.

Other resources that might be of interest to you.
Podcast: Partnering with US Signal
Episode Summary In this episode, Pat Cannon, Field CTO at US Signal, joins Art Ocain. With 10+ years of Cloud Architecture experience at US Signal, Pat gives us great insight on what US signal offers, how partnering with Airiam helps improve b
Vivian Lee
>>Read More
HIPAA Technology Services
The Health Insurance Portability and Accountability Act (HIPAA) was passed by Congress in 1996. This was the first time that generally accepted standards for the security and protection of health information were brought into existence. In 2009, HITECH
Vivian Lee
>>Read More
Podcast: The Basics of Cyber Resilience
Episode Summary Cyber resilience is an evolution in mindset for the world of information security. It has been happening for years. Relying on firewalls, anti-virus, and other preventive manners at the expense of planning for what if can mean that a
Conor Quinlan
>>Read More
