Below are the instructions for adding your Exchange Email Account to your Android Phone. If you have any questions or problems, please contact us.
- Touch Apps.
- Touch Settings.
- Scroll to and touch Accounts.
- Touch Add Account.
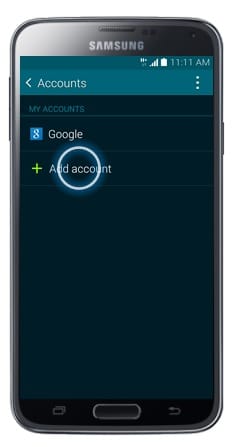
- Touch Microsoft Exchange ActiveSync.
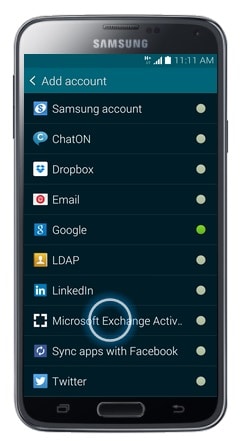
- Enter your workplace email address.
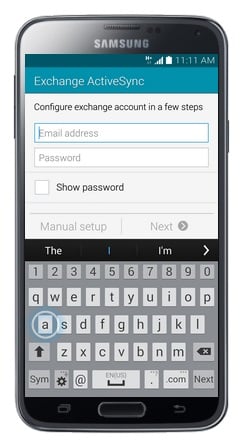
- Touch Password.
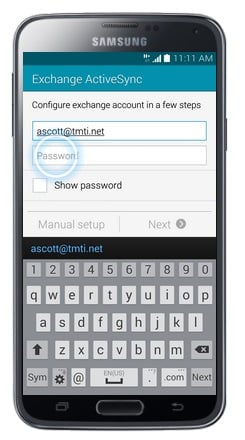
- Enter your email account Password.
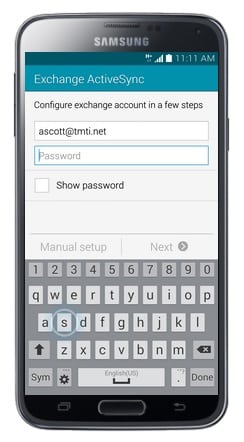
- Touch Next.
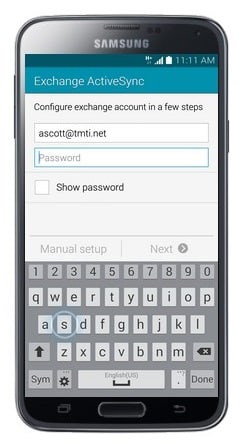
- Touch Domain\username.
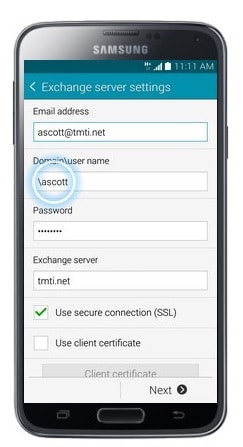
- Leave the Domain blank. Just type in \username. This is the first part of your email address before the “@” sign.
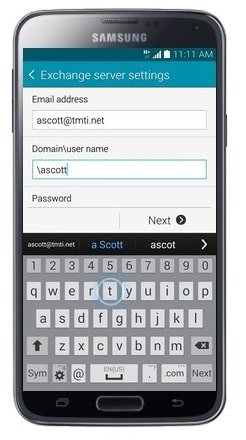
- Scroll to and touch Exchange Server.
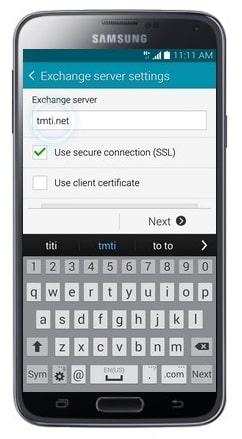
- Enter the Server address. (The Server for Office 365 is: outlook.office365.com)
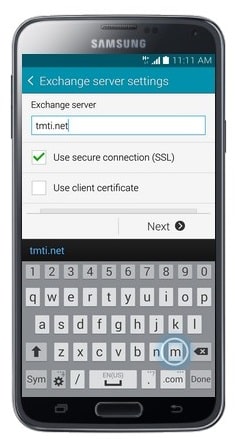
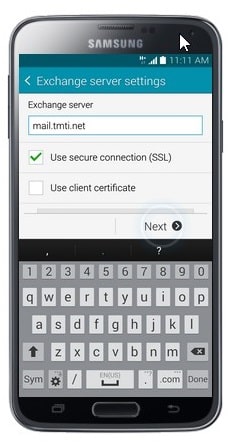
- Touch Next.
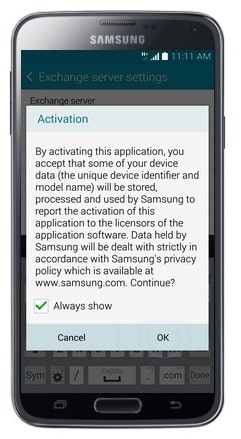
- Touch OK.
- Wait while the phone verifies the account.
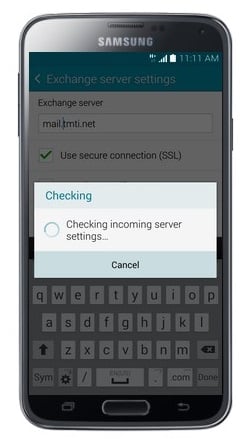
- Touch OK.
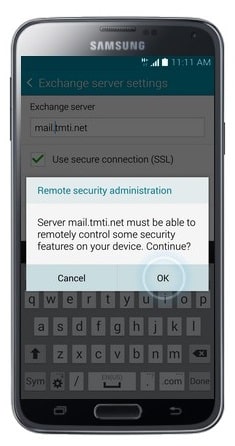
- Scroll down and touch Next. Some options will be pre-selected. You can change any of the displayed options before proceeding.
<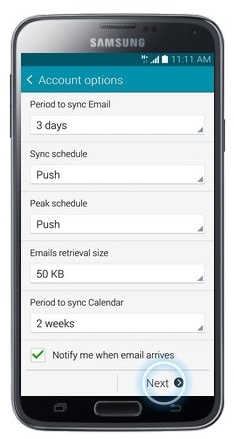
- Touch Activate.
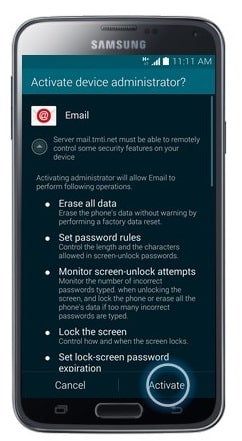
- Edit the Account Name if desired.
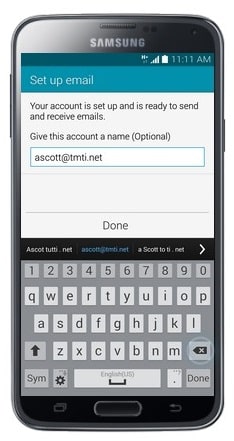
- Touch Done.
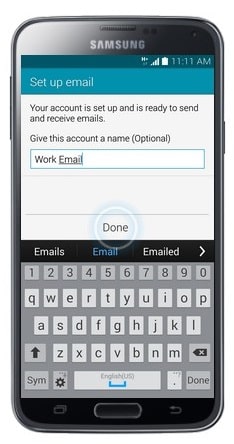
- The email account has been added. To view the email account, press the Home button.
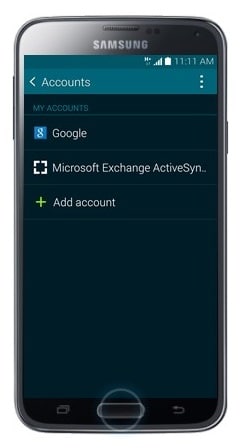
- Touch Apps.
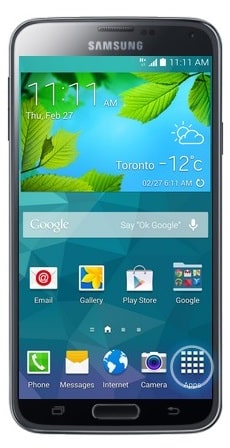
- Touch Email. Your email will sync to your phone once you touch the Email button.